In 2025, Augur saw unprecedented growth in identifications and confirmations as AI-powered threat actors increased the speed, scale, and complexity of modern cyberattacks.
Cisco’s 2025 Cybersecurity Readiness Index found that 86% of organizations surveyed say they’ve experienced AI-related security incidents in the last 12 months. And in its 2026 Tech Trends & Priorities Pulse Poll, based on responses from nearly 3,000 global cybersecurity, audit, risk, and compliance professionals, ISACA found that almost six in ten said AI-powered cyber threats will “keep them up at night” next year.
The increases in malicious activity and the sheer number of novel threats being generated have put SOCs under pressure and made preemptive cybersecurity top-of-mind for security leaders (learn more about preemptive cybersecurity here). And AI isn’t just being used to power attacks, Augur is also tracking and protecting against threat actors (eg, SweetSpecter, Lazarus Group, Lapsus$, Kimsuki and APT 41) who are actively targeting corporate AI investments. And if you needed any further corroboration, the Anthropic case provided insight into where things are headed.
Augur is taking a leadership role in the preemptive cybersecurity space, delivering unique, highly actionable protection ahead of cyberattacks. And, for the first time, Gartner® recognized Augur Security in its Emerging Tech Impact Radar: Preemptive Cybersecurity report.
Let’s take a look at what Augur saw last year.
Augur By The Numbers
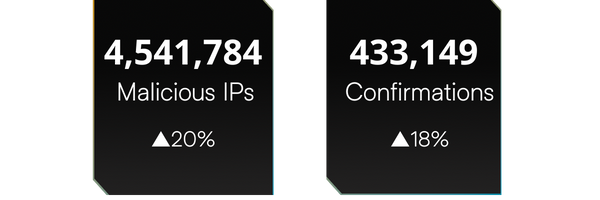
In 2025, Augur’s patented ML uncovered 4.5+ million new malicious IPs before they were operationalized by threat actors. This marks a 20% year-over-year increase and the largest annual total in Augur’s history. Independent third-party confirmations also climbed over 18%, reinforcing the reliability of Augur’s preemptive approach.
Since its launch, Augur has built a living knowledge base of more than 15 million malicious IPs, including 12 million unreported and unique to Augur. This intelligence represents the single deepest source of preemptive cybersecurity insights.
Major Threat Campaigns Disrupted by Augur in 2025
Augur identifies thousands of new threats every month. Here are a few of the front-page cyberattacks Augur preempted in 2025.
Scattered Spider
Augur identified four key IPs (belonging to 3 separate IP ranges) attributed to Scattered Spider (an APT targeting retail and transportation sectors). Augur flagged and blocked the infrastructure months ahead of the latest wave of attacks, shielding a major telecom client from 49 attempted breaches. Read the blog
Sharepoint
Nation-state actors exploited a new SharePoint RCE chain known as ToolShell to hijack servers and extract cryptographic keys to gain admin access and long-term persistence. Targets include U.S. agencies, energy firms, and universities. Augur flagged a key IP address used in the attacks over 360 days before first attacks and protected our customers! Read the blog
Taiwan Semi-Conductor Sector (UNK_FistBump, UNK_DropPitch, UNK_SparkyCarp)
In July, Proofpoint reported that China-linked groups have increased phishing attacks on Taiwan’s semiconductor sector. UNK_FistBump targeted chip companies with job-themed lures, UNK_DropPitch focused on financial analysts covering the sector, and UNK_SparkyCarp used credential phishing through custom adversary-in-the-middle kits. Augur identified five key IPs associated with the campaign, an average of 300+ days ahead of the Proofpoint report. Take a deep dive in our 3-part investigation: Blog 1, Blog 2, Blog 3
Salesforce / Salesloft
Augur identified and preempted 16 malicious IPs related to an UNC6040 and UNC6395 campaign first reported in an FBI Flash in September. The campaign targeted Salesforce environments through social engineering, OAuth/connected-app abuse, and stolen tokens. The IPs were identified by Augur at least seven months before they were listed in the FBI Flash, protecting our clients long before the attacks began. Read the blog
F5 /Big-IP
Between 2023 and 2025, multiple China-linked threat actors systematically targeted F5 BIG-IP, Ivanti, and other edge infrastructure devices—blending espionage, source code theft, and long-term persistence across enterprise and government networks. Augur identified and blocked 4 key IPs tied to these campaigns more than a year in advance, protecting customers before public disclosures and active exploitation began. Read the blog
DPRK IT Workers / BeaverTail Malware
DPRK operators blend fraudulent employment, insider access, and APT-level tradecraft to conduct espionage, data theft, and revenue generation. With operations now expanding across the United States and Europe, this threat represents one of the most significant and persistent enterprise-level risks of the past five years. Augur identified and blocked 8 IPs (from 5 separate CIDRs) associated with the campaign more than a year in advance. Read the blog
Stay Tuned for Big Things in 2026
AI-powered threats will only accelerate in 2026, with broad industry consensus that this is the year their disruptive potential truly comes into focus. At Augur, we are doubling down on our native AI foundation to identify and preempt even more threats.
We’re also investing to expand Augur’s preemptive cybersecurity platform by adding richer context, associations, Agentic detection and investigative workflows on top of our early-warning infrastructure. That includes broader visibility across domains (brand protection), certificates, and exposed assets, so security teams get a continuous, internet‑wide view of attackers and the malicious infrastructure being spun up against them.
Follow us on LinkedIn to stay up to date with all the latest Augur News.


.png)

