EXECUTIVE SUMMARY
This threat intelligence assessment examines the infrastructure enablers behind China-linked cyber espionage operations targeting Taiwan's semiconductor sector from 2024 to 2025. The analysis focuses on AS21100 (GREEN FLOID LLC) and its role in facilitating advanced persistent threat activities.
Taiwan's semiconductor industry accounts for 92% of global advanced chip manufacturing, making it a prime target for Chinese cyber-espionage operations aimed at achieving technological self-sufficiency. At least four distinct China-aligned APT groups actively targeted Taiwan's semiconductor ecosystem between March and June 2025, representing a significant escalation from sporadic historical activity.
GREEN FLOID LLC maintains connections to both Russian disinformation operations (2017 Internet Research Agency) and current China-linked cyber operations, demonstrating how bulletproof hosting providers enable cross-jurisdictional threat activities. Augur Security's platform identified malicious infrastructure associated with these campaigns an average of 51 days before traditional threat intelligence sources, enabling proactive defense measures.
1. INTRODUCTION
Previous articles in this series traced China-linked phishing campaigns against Taiwan's semiconductor sector to hosting infrastructure supplied by CHELYABINSK-SIGNAL-AS. What initially appeared to be a fringe network in Russia's industrial hinterland revealed a recurring pattern: regional infrastructure leased to the same reseller cluster, then repurposed for malware distribution, staging domains, and proxy access. The overlap between ProfitServer operations, ITC holdings, and targeted intrusion activity was too consistent to dismiss as a coincidence.
This assessment focuses on AS21100 - GREEN FLOID LLC, a critical infrastructure provider identified in Augur's preemptive threat detection system. The analysis examines the organization's evolution from supporting Russian information operations to facilitating current China-linked APT activities, providing actionable intelligence for defensive operations.
2. GEOPOLITICAL AND STRATEGIC CONTEXT
2.1 Taiwan's Semiconductor Significance
Taiwan's semiconductor industry occupies an unparalleled position in global technology supply chains. Taiwan Semiconductor Manufacturing Company (TSMC) fabricates 92% of the world's most advanced chips using sub-7nm process nodes. The economic scale is staggering: Taiwan's semiconductor output reached NT$5 trillion (US$162.9 billion) in 2024, with projected 20% growth to NT$6.3 trillion in 2025. This growth is primarily driven by the AI revolution, with TSMC's 3-nanometer chip shipments increasing by 60% in 2025 and AI chip volumes surging 12-fold since 2021.
The strategic vulnerability is profound. A Chinese takeover of Taiwan would threaten US$10 trillion in global economic losses and severely impact US, Japanese, and allied national security interests. This makes Taiwan's semiconductor facilities among the most geopolitically sensitive industrial assets globally.
2.2 China's Strategic Imperatives
China's cyber espionage targeting of Taiwan's semiconductor sector aligns with multiple strategic objectives. The 'Made in China 2025' initiative aimed for 40% domestic semiconductor content by 2020 and 70% by 2025. Despite significant investment, China achieved only approximately 6% domestic production capacity by 2024, leaving it dependent on Taiwanese manufacturing for 70% of its deficit. This failure has intensified Beijing's reliance on alternative methods to acquire semiconductor technology.
US-led multilateral restrictions, coordinated through the Department of Commerce and involving Japan, the Netherlands, South Korea, and Taiwan, have severely limited China's access to advanced lithography equipment and sub-7nm manufacturing technology. These export controls have created a technology chokepoint that China cannot easily circumvent through legitimate channels. Cyber espionage provides an alternative pathway to acquire restricted technical knowledge that would otherwise take decades of indigenous development.
President Xi Jinping's 14th Five-Year Plan (2021-2025) emphasizes domestic innovation through the 'dual circulation strategy' while engaging selectively with global markets. Theft of semiconductor technology directly supports this economic policy framework. Additionally, advanced semiconductors are critical for AI-driven military systems, hypersonic weapons, quantum computing applications, and defense-related computing capabilities that underpin China's military modernization goals.
3. AS21100 - GREEN FLOID LLC: INFRASTRUCTURE ANALYSIS
3.1 Organizational Profile
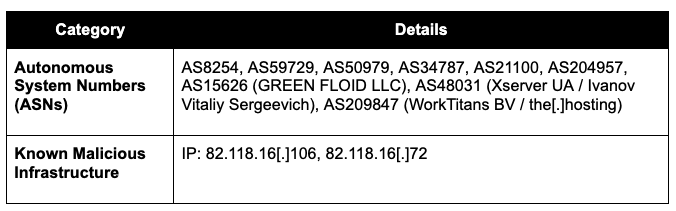
Green Floid LLC operates as a US-based internet service provider specializing in hosting, proxy solutions, and virtual private servers. The organization maintains operations under multiple Autonomous System Numbers, reflecting an extensive and geographically distributed network infrastructure: AS8254, AS59729, AS50979, AS34787, AS21100, AS204957, and AS15626. These ASNs maintain presence across the United States, Bulgaria, Russia, Ukraine, Seychelles, the UAE, the United Kingdom, and Hong Kong.
The company was incorporated in Florida on March 20, 2015, originally under the name ITLDC. Its network scale includes approximately 12,544 IPv4 addresses and extensive IPv6 allocations, hosting over 24,000 domains. With a global AS ranking of 3,392 and server locations in Kharkiv (Ukraine), Amsterdam (Netherlands), and Los Angeles (USA), Green Floid maintains a significant international footprint.
Scamalytics rates Green Floid LLC as a medium fraud risk ISP with a risk score of 37/100, indicating that approximately 37% of observable web traffic from this provider is suspected to be potentially fraudulent. This elevated risk score places Green Floid well above legitimate hosting providers and suggests a significant portion of its customer base engages in malicious or fraudulent activities.
3.2 Internet Research Agency Connection
In 2017, Green Floid LLC operated as a branch of ITL Networks (AS15626), which subsequently rebranded as GREEN FLOID LLC following CNN's investigative report linking ITL Networks to Russian troll sites and the Internet Research Agency. The original CNN article, published in 2017 and accessible via archive.org until September 12, 2024, detailed how Russian-operated troll websites aimed at exacerbating US debates on race and policing remained online with support from American-based internet companies.
Routing records pointed to Green Floid LLC (Florida) and Ukrainian hosting provider ITL Networks as infrastructure providers hosting or relaying traffic for IRA-operated sites, including 'Don't Shoot Us' and 'Black Matters.' These operations aligned with the Internet Research Agency playbook, utilizing fake personas, social media pages, and targeted advertising to exacerbate political and social divisions within the United States during the 2016 election cycle.
The ITL Networks executive, interviewed by CNN, stated that tracking all customers was impossible and confirmed that Special Counsel Robert Mueller's investigators had not contacted the company, although he expressed a willingness to cooperate. This pattern of plausible deniability is common among bulletproof hosting providers who maintain they cannot monitor all customer activities while simultaneously cultivating reputations for ignoring abuse complaints.
3.3 Network Relationships and Bulletproof Hosting Connections
ITL Networks CEO Dmitry Deineka advertises his ownership on Facebook and maintains a personal website that documents his business trips to Bulgaria and computer-related activities. Social media analysis reveals connections to Vitaly Ivanov, owner of Xserver UA (AS48031), with both individuals based in Kharkiv, Ukraine. This personal connection between executives of related hosting providers suggests coordinated operations rather than arm's-length business relationships.
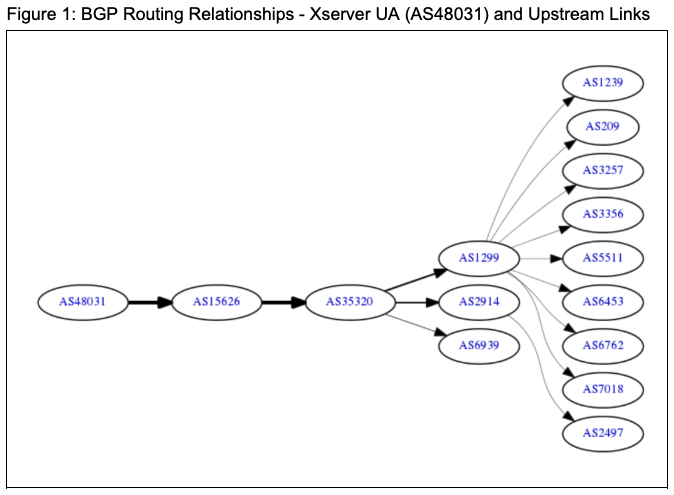
This network diagram from 2017 illustrates the BGP routing relationships between Xserver UA (AS48031) and its upstream provider ITL Networks (AS15626), now rebranded as GREEN FLOID LLC.
Dmitry Deineka, CEO of ITL Networks (now GREEN FLOID LLC), publicly advertises his ownership and business activities on his Facebook profile, including business trips to Bulgaria and technical interests.
Xserver UA previously served as the upstream provider to ITL Networks (AS15626) through 2017. Current operations continue under the name 'Ivanov Vitaliy Sergeevich' with GREEN FLOID LLC (AS15626) maintained as upstream provider. Security researchers classify Xserver as a bulletproof hoster based on its apparent disregard for illicit content on their network and consistent hosting of malicious campaigns, including portions of the Avalanche botnet infrastructure. The Avalanche network was one of the largest cybercrime infrastructures ever documented before its 2016 takedown, and Xserver's continued operation of related infrastructure demonstrates the resilience of bulletproof hosting operations.
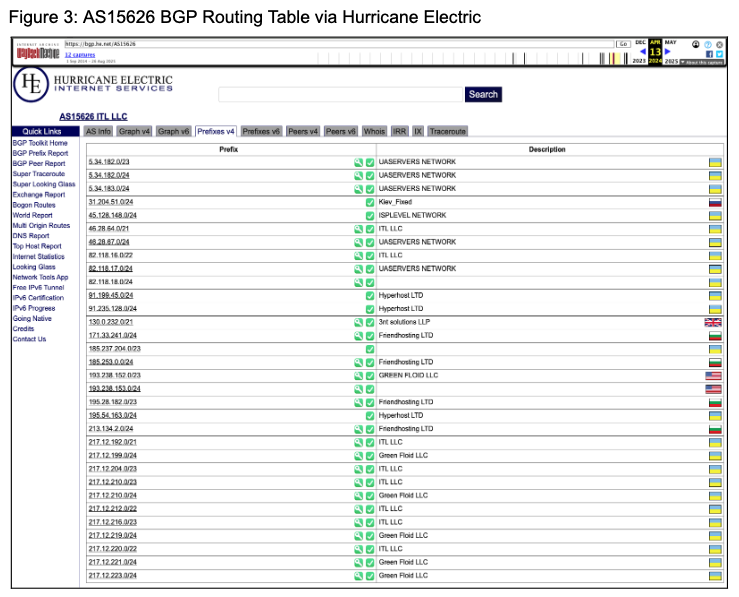
Hurricane Electric BGP toolkit screenshot showing AS15626 (ITL LLC) prefix allocations, demonstrating the extensive network infrastructure controlled by GREEN FLOID LLC entities, including connections to UASERVERS NETWORK, Friendhosting LTD, and other associated networks across multiple geographic regions.
3.4 PQ Hosting Plus Connection
Investigative research by Brian Krebs documented Green Floid LLC's infrastructure connections to PQ Hosting Plus, formerly known as Stark Industries Solutions, a major bulletproof hosting operation that materialized two weeks before Russia's February 2022 invasion of Ukraine. Stark Industries rapidly became the epicenter of massive DDoS attacks against Ukrainian and European government and commercial targets, particularly those conducted by the pro-Russia hacktivist group NoName057(16).
An analysis of IP address ranges in May 2024 revealed the largest concentration of Stark Industries' infrastructure in the Netherlands, followed by Germany and the United States. Stark Industries was connected to approximately 4,600 Internet addresses listing Comcast Cable Communications as the owner, all of which were linked to Proxyline, a Russian proxy service advertising over 1.6 million global proxies available for rent. Network mapping by Spur.us revealed two ISPs appearing repeatedly throughout Proxyline address ranges: Kharkiv-based ITL LLC (Information Technology Laboratories Group) and Miami-based Green Floid LLC.
The European Union sanctioned Stark Industries' primary conduit, PQ Hosting (Moldovan), and its owners, Yuri and Ivan Neculiti, in May 2025 for links to Russia's hybrid warfare efforts. However, the sanctions proved ineffective. Just prior to the sanctions announcement, Stark rebranded to 'the[.]hosting' under Dutch entity WorkTitans BV (AS209847) on June 24, 2025. This rapid infrastructure migration highlights the challenge of disrupting bulletproof hosting operations solely through sanctions, as operators can quickly reestablish operations under new legal entities while maintaining the same technical infrastructure and customer relationships.
The FIN7 cybercrime group, responsible for an estimated $3 billion in losses since 2013, resurrected its operations in 2024 by leveraging Stark Industries' infrastructure. After US authorities declared FIN7 defunct in 2023 following the convictions of high-level members, the group re-emerged by registering thousands of typosquatting domains that mimicked those of media and technology companies. These domains were overwhelmingly hosted on Stark Industries' infrastructure, demonstrating how bulletproof hosting enables rapid reconstitution of cybercrime operations even after successful law enforcement actions.
4. Conclusion
The 2024-2025 China-linked cyber espionage campaigns targeting Taiwan's semiconductor industry represent a significant escalation in both volume and sophistication. The deployment of at least four distinct APT groups within a three-month period demonstrates strategic coordination and prioritization at the national level. This concentrated effort reflects China's recognition that traditional pathways to semiconductor technology acquisition through legitimate investment, research collaboration, and commercial relationships have been largely closed by US-led export controls and heightened security awareness.
GREEN FLOID LLC's infrastructure serves as a critical enabler for diverse malicious activities spanning Russian information operations, cybercrime facilitation, and current China-linked APT campaigns. The organization's evolution from supporting 2017 Internet Research Agency operations to hosting infrastructure for Stark Industries Solutions and FIN7 cybercrime operations demonstrates the persistent threat posed by bulletproof hosting providers operating with apparent impunity. The personal and corporate connections between GREEN FLOID LLC, ITL Networks, Xserver UA, and related entities reveal a coordinated ecosystem rather than independent operations.
Augur Security's preemptive threat detection platform enables organizations to transition from a reactive to a proactive cybersecurity posture. The platform's demonstrated ability to identify attack infrastructure, on average, 51 days before weaponization, combined with a near-zero false positive rate, addresses the fundamental limitations of traditional threat intelligence approaches. The operational track record against major campaigns, including SolarWinds, Colonial Pipeline, and Volt Typhoon, provides confidence that similar preemptive detection would have been effective against the 2025 Taiwan semiconductor targeting.
Taiwan's semiconductor industry holds a pivotal position in global technology supply chains and is a critical component of allied national security architectures. Protecting this strategic asset requires the comprehensive adoption of preemptive threat intelligence, enhanced collaboration among industry and government stakeholders, and sustained international coordination to disrupt the bulletproof hosting infrastructure that enables adversary operations. The geopolitical stakes have never been higher, as control of advanced semiconductor manufacturing capabilities will fundamentally shape the balance of economic and military power in the 21st century.
The recommendations outlined in this assessment provide a framework for strengthening defensive capabilities against China-linked APT operations while establishing sustainable security practices for an evolving threat landscape. Organizations that implement these measures will significantly reduce their exposure to sophisticated cyber espionage campaigns and contribute to the collective defense of Taiwan's semiconductor ecosystem. However, defensive measures alone cannot eliminate the threat. Long-term security requires sustained investment in preemptive technologies, continuous adaptation to evolving adversary tactics, and unwavering commitment to information sharing and collaborative defense across the global semiconductor industry.
5. Recommendations
5.1 Immediate Actions for Semiconductor Sector Organizations
- Adopt preemptive cybersecurity tools such as Augur to bolster traditional Detection and Response ahead of first attacks and reduce alert noise in the SOC
- Implement network-level blocking for:
- GREEN FLOID LLC ASNs: AS8254, AS59729, AS50979, AS34787, AS21100, AS204957, AS15626
- Xserver UA (AS48031)
- Stark Industries Solutions / the[.]hosting (AS209847)
- Known malicious infrastructure:
- IP 45.141.139[.]222 (UNK_FistBump C2)
- Domain accshieldportal[.]com (UNK_SparkyCarp)
- Accept measured false-positive risk when blocking high-risk ASNs due to documented malicious activity and fraud classifications.
- Strengthen email security through behavioral analysis–based filtering and authentication protocols (DMARC, SPF, DKIM).
- Visually flag external email and require out-of-band verification for sensitive or credential-related requests.
- Provide specialized spear-phishing awareness training tailored to semiconductor-sector targeting techniques (e.g., UNK_ColtCentury legal department lure campaigns).
- Extend security requirements and intelligence sharing to smaller suppliers and chemical companies.
- Establish minimum cybersecurity requirements and perform recurring supplier security assessments.
- Apply network segmentation to limit lateral movement if a supply chain partner is compromised.
- Deploy mandatory hardware-based MFA (FIDO2, WebAuthn) for all sensitive access.
- Avoid SMS and software token–based authentication, which are vulnerable to adversary-in-the-middle attacks demonstrated by UNK_SparkyCarp.
5.2 Medium-Term Strategic Initiatives
- Begin zero-trust implementation with:
- Microsegmentation
- Continuous access verification
- Strict least-privilege enforcement
- Software-defined perimeter for remote manufacturing and R&D access
- Establish a dedicated internal threat hunting program focused on:
- China-linked APT behavioral indicators
- Preemptive intelligence (ex: Augur-derived hypotheses)
- Regular APT-scenario tabletop exercises
- Enhance Endpoint Detection and Response capabilities to detect:
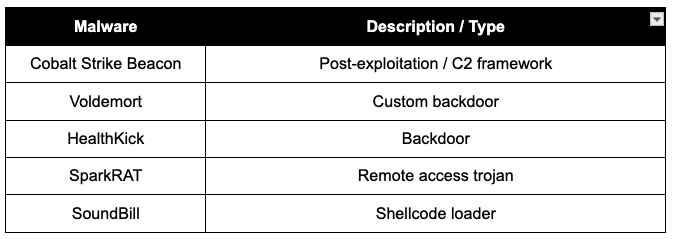
- DLL sideloading techniques (ex: UNK_FistBump)
- Cobalt Strike behaviors
- Custom malware backdoors
- Misuse of legitimate cloud services (Google Sheets C2)
- Deploy comprehensive Data Loss Prevention strategies to protect semiconductor IP including:
- Monitoring for design, R&D and process exfiltration
- Insider threat detection programs
- Encryption of sensitive data at rest and in transit using hardware security modules
- Air-gapped networks for highly sensitive R&D environments
- Extend IP protection practices to legal and administrative staff with access to patents, licensing, and confidential agreements.
7. Indicators of Compromise
Network Infrastructure
Malware Families and Techniques
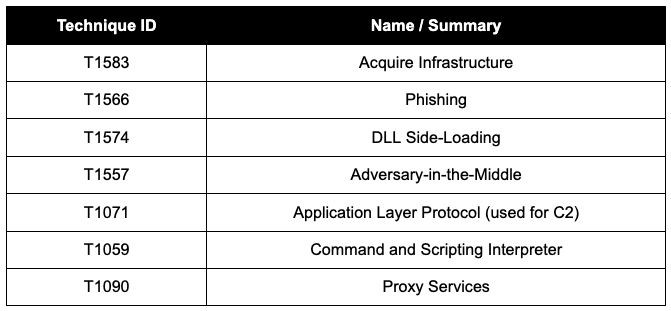
MITRE ATT&CK Techniques
8. Sources
- Proofpoint Research (July 2025): “Phish and Chips: China-Aligned Espionage Actors Ramp Up Taiwan Semiconductor Industry Targeting” https://www.proofpoint.com/us/blog/threat-insight/phish-china-aligned-espionage-actors-ramp-up-taiwan-semiconductor-industry-targeting
- Cisco Talos (August 2025): “UAT-7237 targets Taiwanese web hosting infrastructure” https://blog.talosintelligence.com/uat-7237-targets-web-hosting-infra/ Talos Intelligence Blog
- KrebsOnSecurity (May 2024): “Stark Industries Solutions: An Iron Hammer in the Cloud” https://krebsonsecurity.com/2024/05/stark-industries-solutions-an-iron-hammer-in-the-cloud/ Krebs on Security
- KrebsOnSecurity (September 2025): “Bulletproof Host Stark Industries Evades EU Sanctions” https://krebsonsecurity.com/2025/09/bulletproof-host-stark-industries-evades-eu-sanctions/ Krebs on Security
- The Stimson Center (2025): “Tariffs, Economic Nationalism, and the Future of U.S. Semiconductor Manufacturing”
- https://www.stimson.org/2025/tariffs-economic-nationalism-and-the-future-of-us-semiconductor-manufacturing/ Stimson Center
- The China US Focus (October 2025): “China’s Strive for Self-Reliance in Advanced Technology” https://www.chinausfocus.com/peace-security/chinas-strive-for-self-reliance-in-advanced-technology China-US Focus




