Introduction
In recent months, China-linked groups have intensified phishing attacks targeting Taiwan's semiconductor industry. Between March and June 2025, several distinct campaigns emerged: UNK_FistBump used job lures, UNK_DropPitch targeted financial analysts, and UNK_SparkyCarp employed custom adversary-in-the-middle kits for credential theft. These operations demonstrate a comprehensive intelligence-gathering effort that extends beyond technical firms to encompass financial institutions as well.
While UNK_FistBump shares some traits with TA415, differences in tools and command-and-control methods suggest it's a separate group. Other China-linked actors, such as UNK_ColtCentury, also continued to target legal staff within the industry, reflecting an ongoing interest in various roles.
In Part 1 of this series, we identified a subset of the malicious infrastructure that threat actors used to launch their attacks. See below in Table 1. In Part 2, we focus on one of the hosting providers, CHELYABINSK-SIGNAL-AS.
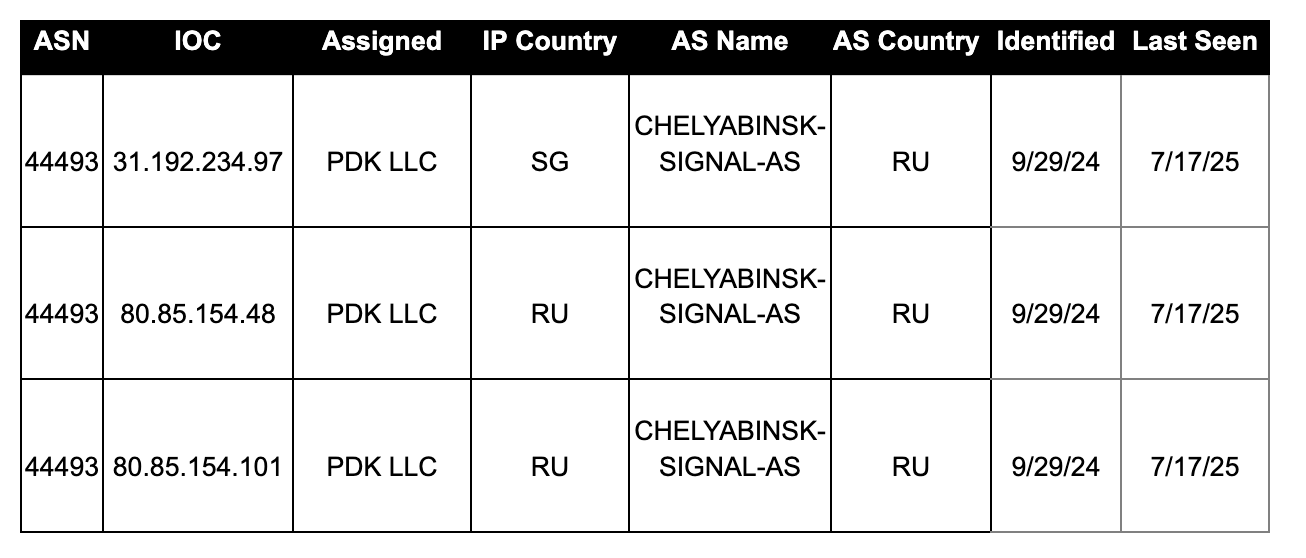
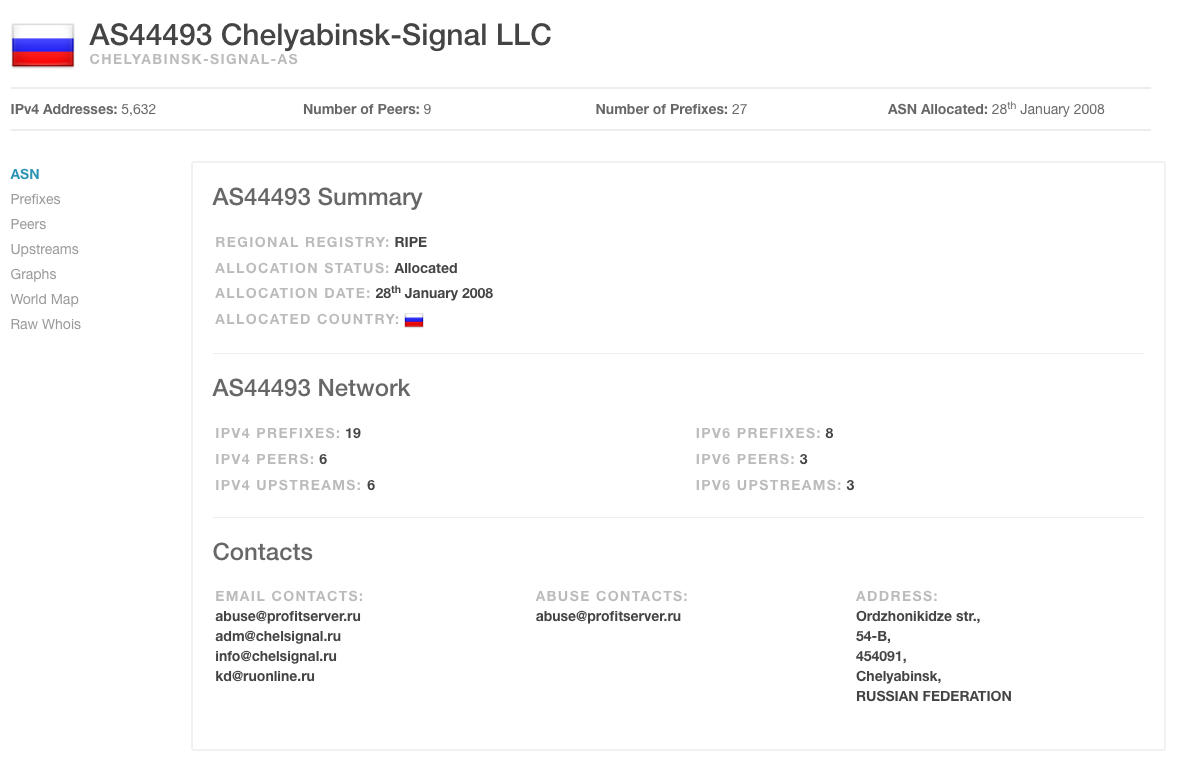
AS44493 - CHELYABINSK SIGNAL
Chelyabinsk is a city in Russia with a population of about 1.1 million. It is east of the Ural Mountains, roughly 90 km from the Kazakhstan border, a drive of about one and a half hours. The city is situated on the border between Europe and Asia. Chelyabinsk is not known for its technology sector, but it is a major center for heavy industry, metallurgy, and defense-related manufacturing. The city has reliable internet and transportation, but is far from global internet hubs and the main data center networks. As of now, it currently announces 19 IPv4 prefixes, totalling 7,168 IP addresses. These are used across different hosting and infrastructure services. In network telemetry, these blocks can be linked to suspicious or harmful activity either through bulletproof hosting, resold blocks, or other factors.
Organization Overview
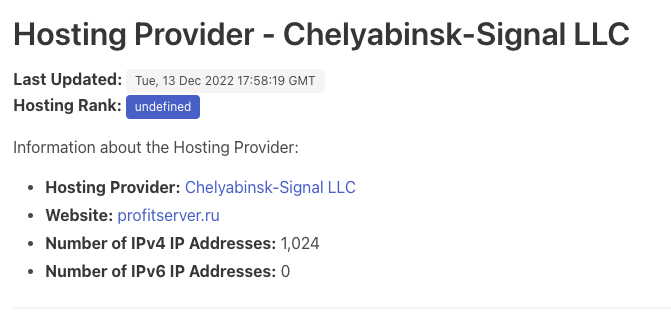
Chelyabinsk-Signal LLC is a regional IT or telecom provider based in this industrial city. Its presence is mainly local or domestic. The name “Signal” may reflect telecom, support for industry, or government. Given the region’s military and manufacturing history, the company may have handled communications infrastructure for industrial or state projects such as Cybersecurity Center LLC.
Cybersecurity Center LLC, also known as OOO TSKB, is a Russian limited liability company headquartered in Chelyabinsk (Generala Martynova St., 3, Room 1) with Tax ID No. 7448223757 and Registration Number 1207400010905. The entity has been added to U.S. sanctions under Executive Order 14024, which targets organizations that support Russia’s military-industrial complex. It carries a secondary sanctions risk, meaning non-U.S. persons dealing with it may also be exposed to restrictions. In addition to the United States, multiple jurisdictions, including Canada, Switzerland, the European Union, the United Kingdom, Australia, New Zealand, and Japan, have imposed sanctions against this company.
Regional and Risk Considerations
Chelyabinsk-Signal LLC has remained a small, persistent network entity since 2008. Its size and routing patterns do not match those of a tier-1 provider or major content network. Instead, it may serve niche or abuse-tolerant roles. Chelyabinsk’s location close to Kazakhstan and east of the Urals means its infrastructure is distant from Russia’s largest internet exchanges in Moscow and St. Petersburg. While the city’s internet backbone is reliable, this geographic distance can make Chelyabinsk attractive for lower-profile operations, including advanced persistent threat activity. Since mid-2023, both cyber and drone attacks linked to Ukraine have targeted assets in this region. For example, in August 2024, Ukrainian Defense Intelligence and hackers from the “VO Team” targeted the Vega Company in Snezhinsk (Chelyabinsk region), which serviced the All-Russian Scientific Research Institute of Technical Physics (VNIITF). The attack reportedly disabled ~1,173 switches and 10 servers, destroyed data on Vega’s servers, and disrupted communications for nearly a week. Also in June 2025, reports emerged, though unconfirmed, that a warehouse in Chelyabinsk was being used as a staging point to assemble drones for strikes on Russian military air bases. These events underscore the dual risk environment for companies operating in Chelyabinsk: exposure to retaliatory Russian security measures and vulnerability to asymmetric cross-border attacks, both cyber and kinetic.
Potential links to Green Floid LLC
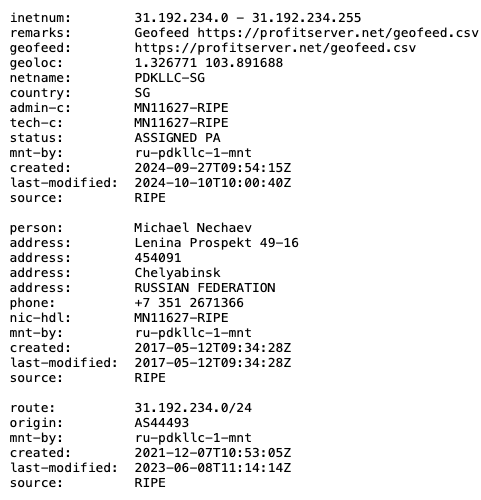
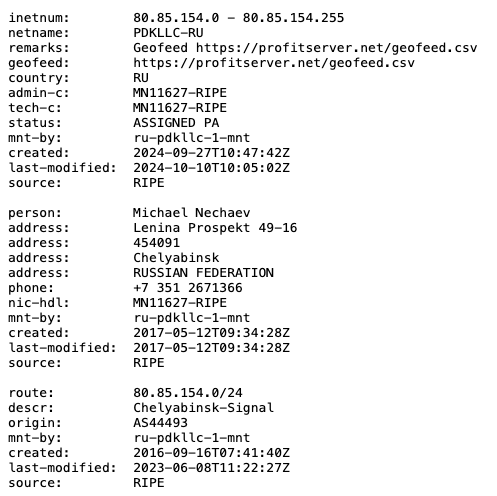
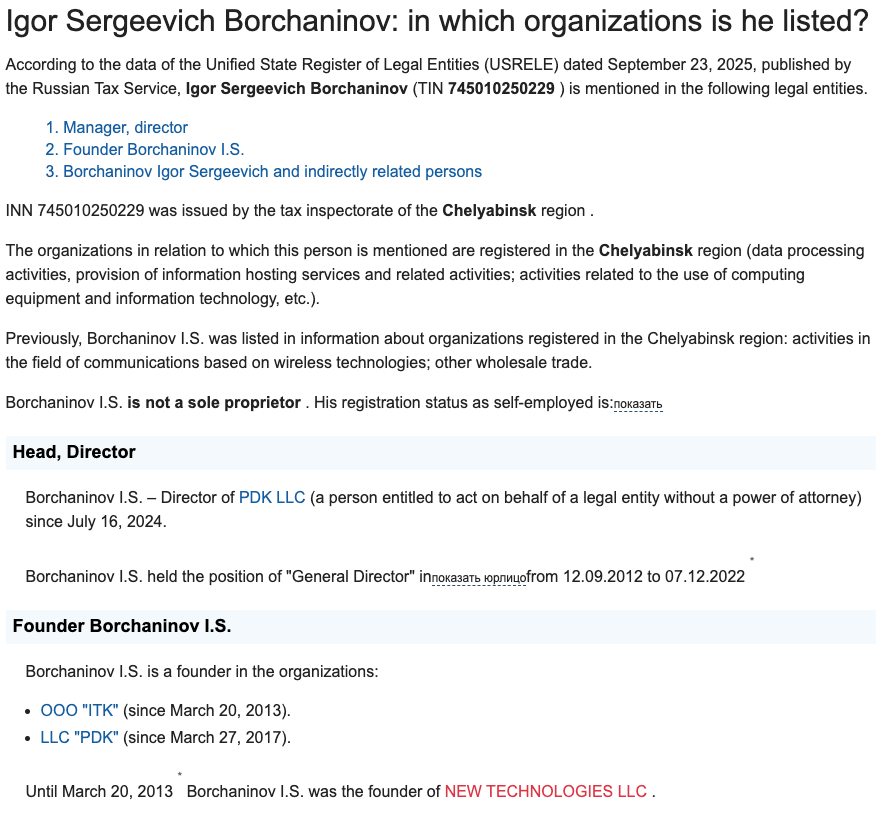
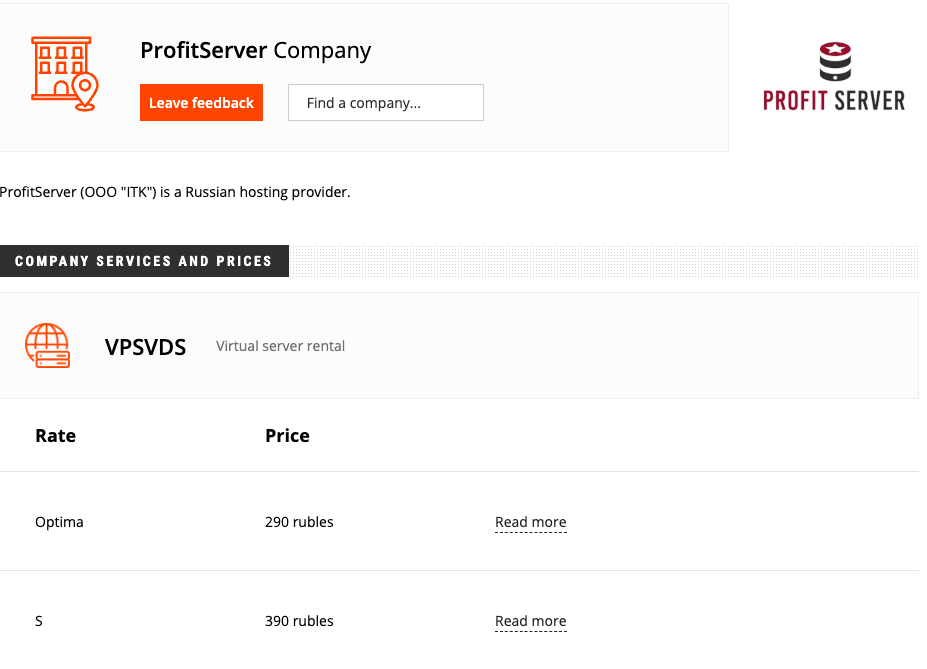
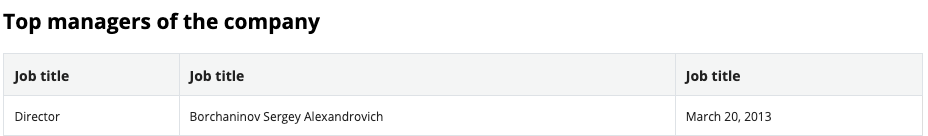
Both CIDRs involved in this campaign have WHOIS information that lists Michael Nechaev as the contact person, representing the hosting provider PDK LLC, also publicly known as ProfitServer. This means that it is likely that CHELYABINSK-SIGNAL leases these CIDRs to PDK LLC.
It is interesting to note that Michael Nechaev has worked for or previously worked with ITL LLC. This is based on information available on his LinkedIn profile. ITL LLC has rebranded itself as Green Floid LLC. Even though it could be that Mr. Nechaev didn’t update his profile, it raises interesting questions, especially regarding the fact that both PDK, LLC and Green Floid LLC were used in this campaign.
CHELYABINSK-SIGNAL, PDK LLC (Profitserver), ITK LLC, DataGear
Records show that all these companies are connected, owned, and operated by the same individuals under a holding named ITC Holding. PDK LLC (Profitserver) appears to operate in Eastern Europe, while DATAGEAR serves Western Europe, as they are located in the UK.
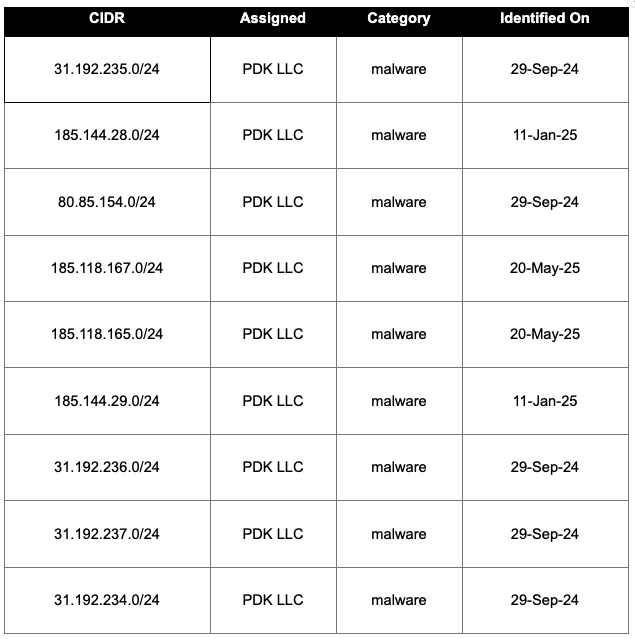
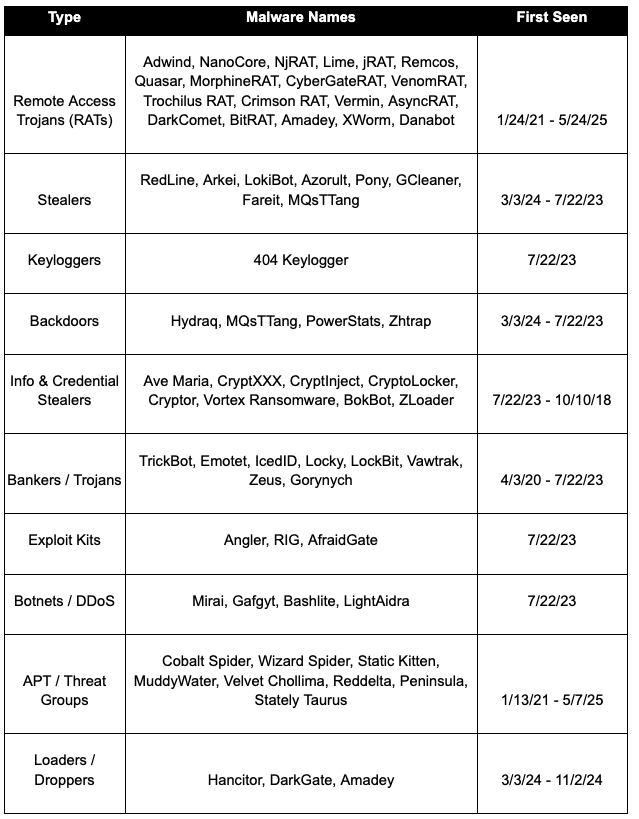
Malware categories and types found on AS44493
Below are the malware categories found on this network CIDRs, along with the instances where Augur preemptively identified them as malicious.
Below are the threat types found on these IP ranges and the dates when they were first seen:
Conclusions and Recommendations
Chelyabinsk-Signal sits at the intersection of low-profile regional hosting and high-frequency malicious use. Its network is neither large nor sophisticated, yet it repeatedly surfaces in activity tied to commodity malware, financially motivated crime, and state-linked targeting. The connection with PDK LLC, Green Floid LLC, and related entities shows that this is less a standalone provider in a remote region of Russia and more an underrated hosting provider conglomerate willing to service or ignore abuse at scale by blurring the lines via the use of multiple LLCs for the same provider.
The same infrastructure that enables credential theft and banking Trojans is also leveraged in phishing operations linked to intelligence collection against Taiwan’s semiconductor sector. That dual utility suggests intent rather than negligence. Whether driven by profit, politics, or both, AS44493 remains an active enabler in campaigns that span criminal and strategic interests.
Any organization monitoring threat infrastructure should treat this ASN and any resources operated by the PDK/ITC Holding cluster as pre-compromised space, rather than neutral IP space.
Stay tuned for PART 3!
Sources
- Ukraine’s Drone Attack: Russian Region Bordering Kazakhstan Cited as Possible Staging Point: https://timesca.com/ukraines-drone-attack-russian-region-bordering-kazakhstan-cited-as-possible-staging-point/
- Cyber Specialists from the Ukrainian Defense Intelligence Have Paralyzed a Russian Nuclear Warhead Developer: https://odessa-journal.com/cyber-specialists-from-the-ukrainian-defense-intelligence-have-paralyzed-a-russian-nuclear-warhead-developer
- Sanctions Database: https://sanctions.lursoft.lv
- STRATLink Sanctions Portal: https://stratlink.meci.gov.cy
- War Sanctions Database: https://war-sanctions.gur.gov.ua
- Chelyabinsk: https://en.wikipedia.org/wiki/Chelyabinsk
- Chelyabinsk, Russia: https://www.britannica.com/place/Chelyabinsk-Russia
- Chelyabinsk, Russia Map: https://www.mapsofindia.com/world-map/russia/chelyabinsk/
- Chelyabinsk Oblast: https://en.wikipedia.org/wiki/Chelyabinsk_Oblast
- Regions: Chelyabinsk: http://www.council.gov.ru/en/structure/regions/CHE/
- Chelyabinsk Oblast: https://peakvisor.com/adm/chelyabinsk-oblast.html
- Chelyabinsk Oblast, Russia: https://www.mindat.org/loc-204646.html
- Chelyabinsk: https://worldglobalatlas.fandom.com/wiki/Chelyabinsk
- Chelyabinsk Oblast: https://www.diy.org/article/chelyabinsk_oblast


.png)

