The acceleration of AI is reshaping the cyber threat landscape faster than traditional security models can adapt. Threat actors are using AI to automate reconnaissance, rapidly weaponize vulnerabilities, and orchestrate multi-wave campaigns that move from discovery to exploitation in days, sometimes hours.
In its recent piece on Preemptive Cybersecurity, Gartner asserts that preemptive cybersecurity represents a critical shift in defensive strategy. Instead of waiting for exploits to trigger alerts after a compromise, preemptive approaches focus on predicting where and how attacks will emerge by identifying threat infrastructure (as Augur does), attacker behavior patterns, and early indicators of future campaigns. Predictive threat intelligence (PTI) extends visibility into the left-of-exploit phase, giving defenders the opportunity to block attacks before they are operationalized.
The recent ToolShell exploitation of on-premises Microsoft SharePoint servers demonstrates why this shift is no longer optional.
Understaning the Exploit
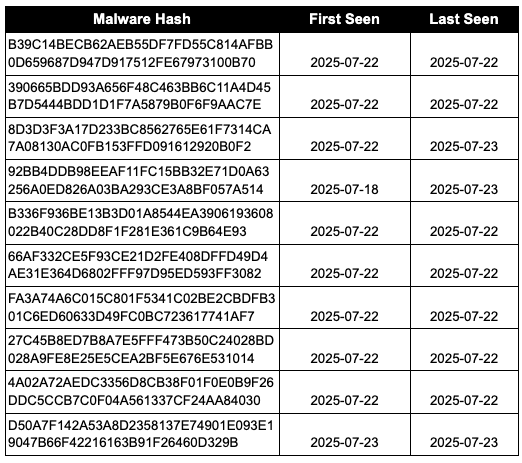
On July 18, 2025, researchers at Eye Security observed a new unauthenticated remote code execution exploit being used to compromise on-premises Microsoft SharePoint servers, dubbed Toolshell by Code White GmbH. The attack targeted nearly 400 servers in the initial wave and continued in subsequent waves, utilizing malicious ASPX backdoors to extract cryptographic MachineKeys for persistent access.
These vulnerabilities enable attackers to gain administrative access, deploy web shells, extract sensitive information, and maintain long-term control of infected SharePoint environments.
ToolShell chains together several flaws:
- CVE‑2025‑49706: an authentication bypass (CVSS 6.5)
- CVE‑2025‑49704: a code injection bug (CVSS 8.8)
- CVE‑2025‑53770: a deserialization vulnerability (CVSS 9.8)
- CVE‑2025‑53771: a path traversal bypass (CVSS 6.5)
Microsoft attributed activity to multiple nation-state actors, including Storm‑2603, Violet Typhoon (AKA APT31), and Linen Typhoon (AKA APT27), with targets spanning U.S. government agencies, universities, telecommunications, and energy firms. Attacks ramped up in mid-July and have continued into late July, often bypassing early mitigations.
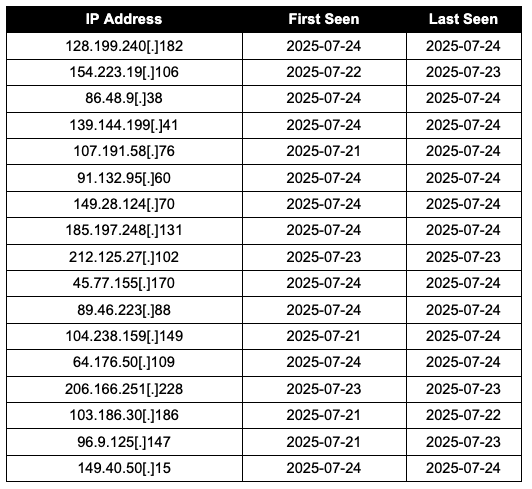
Several of the IP addresses listed below (Table 2) have multiple exploitable vulnerabilities, which would further the theory that attackers used these already compromised systems to launch their attacks against SharePoint Servers. For instance:
- https://www.shodan.io/host/107.191.58.76
- https://www.shodan.io/host/206.166.251.228
- https://www.shodan.io/host/95.179.158.42
Augur identified the IP address 95.179.158[.]42 as malicious more than 360 days ago.

Recommendations
- Install patches for CVE-2025-53770 and CVE-2025-53771 immediately
- Run SharePoint Server 2016, 2019, or Subscription Edition
- Turn on Antimalware Scan Interface in Full Mode and deploy Microsoft Defender Antivirus
- If AMSI can’t be enabled, disconnect the server from the internet or limit access via VPN/proxy
- Deploy it or a similar solution to detect post-exploit activity.
- After updates or enabling AMSI, rotate ASP.NET machine keys and restart IIS on all servers using PowerShell.
- Deploy Augur for preemptive protection against emerging threats
References
- Microsoft SharePoint CVE-2025-49704 / 49706 / 53770: https://unit42.paloaltonetworks.com/microsoft-sharepoint-cve-2025-49704-cve-2025-49706-cve-2025-53770/
- SharePoint Under Siege: https://research.eye.security/sharepoint-under-siege/
- Defending Against ToolShell: https://www.sentinelone.com/blog/defending-against-toolshell-sharepoints-latest-critical-vulnerability
- CVE-2025-53770 and CVE-2025-53771: https://www.trendmicro.com/en_us/research/25/g/cve-2025-53770-and-cve-2025-53771-sharepoint-attacks.html
- Everything You Need to Know: https://www.wiz.io/blog/sharepoint-vulnerabilities-cve-2025-53770-cve-2025-53771-everything-you-need-to-k
- Customer guidance for SharePoint vulnerability CVE-2025-53770:https://msrc.microsoft.com/blog/2025/07/customer-guidance-for-sharepoint-vulnerability-cve-2025-53770/




