EXECUTIVE SUMMARY
This comprehensive threat intelligence report analyzes the convergence of DPRK IT worker operations and BeaverTail/FerretRAT malware campaigns, revealing a sophisticated dual-threat approach that combines insider threats with advanced persistent threat (APT) capabilities. The analysis integrates infrastructure patterns, hosting provider attribution, and operational tradecraft to provide actionable intelligence for defensive operations.
North Korean state-sponsored threat actors have developed a multi-layered operation that generates revenue through fraudulent employment while simultaneously deploying malware for espionage and data theft. Over 300 U.S. companies unknowingly employed DPRK IT workers between 2020 and 2022, with operations expanding globally to Europe between 2024 and 2025. Recent law enforcement actions in July 2025 resulted in the seizure of 137 laptops from 21 laptop farms across 14 U.S. states, underscoring the scale of the infiltration.
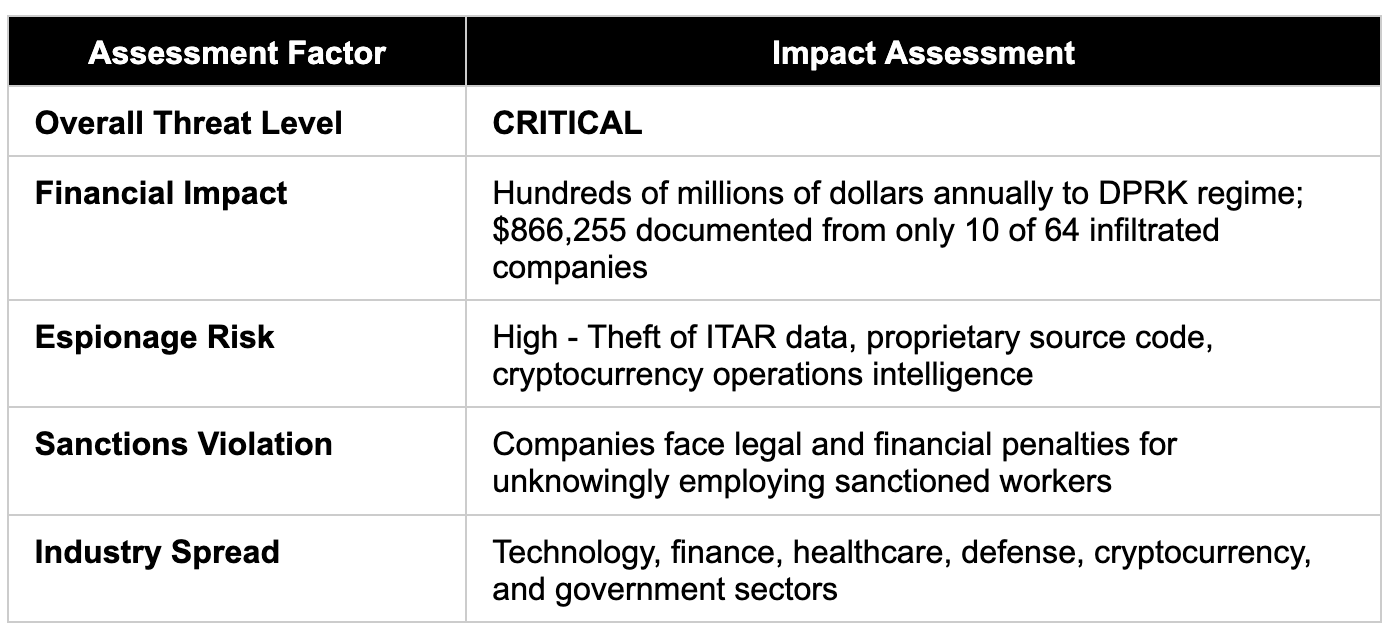
Threat Severity Assessment
Key Findings
- A direct operational link has been confirmed between IT worker employment and the BeaverTail/FerretRAT malware campaigns.
- Over 300 U.S. companies unknowingly employed DPRK IT workers between 2020 and 2022, including Fortune 500 companies.
- Operations expanded to Europe in late 2024, targeting defense and government sectors in Germany, Portugal, and the UK.
- Lazarus Group heavily relies on bulletproof hosting providers Stark Industries (AS 44477) and Belcloud (AS 44901).
- A 100% infection rate has been observed in multiple Stark Industries and Belcloud IP ranges.
- Infrastructure overlap indicates that multiple threat actors (APT42, APT34, APT35, Turla) are leveraging the same bulletproof hosting.
- Since late October 2024, extortion attempts have increased significantly, with terminated IT workers threatening to release sensitive data.
- Individual IT workers earn up to $300,000 annually, with 90% remitted to DPRK regime.
THREAT OVERVIEW
Primary Objectives
- Generate revenue for DPRK weapons of mass destruction (WMD) and ballistic missile programs through fraudulent employment.
- Exfiltrate proprietary information, source code, and sensitive corporate data
- Conduct post-termination extortion by threatening to release or sell stolen data.
- Gather intelligence on defense technologies, cryptocurrency operations, and corporate strategies.
Scale and Scope
Between 2020 and 2022, over 300 U.S. companies across multiple industries, including several Fortune 500 companies, unknowingly employed DPRK IT workers. A January 2025 Justice Department indictment revealed that two North Korean nationals and three facilitators generated at least $866,255 from only ten of at least 64 infiltrated U.S. companies.
The threat expanded significantly in late 2024, with Google Threat Intelligence Group confirming increased operations in Europe, particularly targeting defense and government sectors in Germany, Portugal, and the United Kingdom. Law enforcement operations in July 2025 seized 137 laptops from 21 laptop farms across 14 U.S. states, revealing the extensive logistics network supporting these operations.
Individual IT workers attempted to gain access to information at two government agencies and consistently demonstrated the ability to operate multiple personas simultaneously. In late 2024, one DPRK IT worker was documented operating at least 12 personas across Europe and the United States concurrently.
Evolving Tactics (2024-2025)
- AI-Enhanced Operations: Since 2024, DPRK workers have leveraged AI to enhance photos, replace images in stolen documents, and improve application quality
- Voice Masking: Utilizing voice-changing software during interviews to mask accents and identities
- BYOD Targeting: Since January 2025, targeting Bring Your Own Device (BYOD) environments that lack traditional security and logging
- Increased Extortion: Since late October 2024, recently terminated IT workers have significantly increased extortion attempts, threatening to release sensitive data to competitors.
- Multiple Personas: Operating numerous simultaneous identities across different geographic regions and companies
DUAL-THREAT OPERATION
IT Workers & BeaverTail/FerretRAT Malware Connection
Analysis confirms a direct operational connection between DPRK IT worker employment schemes and BeaverTail malware deployment. Insikt Group tracks PurpleBravo (formerly Threat Activity Group 120), a North Korean-linked cluster that overlaps with the 'Contagious Interview' campaign. The same threat actors employ both legitimate-appearing employment for revenue generation and malware campaigns for espionage and theft, creating a sophisticated dual-threat scenario.
Phase 1: Recruitment
PurpleBravo operators pose as recruiters on LinkedIn, Telegram, and job platforms, contacting software developers about job offers. They claim to represent legitimate companies or create elaborate fake company websites. Operators request that candidates join video interviews and download coding challenges from repositories.
Phase 2: Malware Delivery
The infection chain deploys BeaverTail, functioning as an information stealer and downloader. BeaverTail collects cryptocurrency wallet data, browser credentials, and system information, then downloads and deploys InvisibleFerret, a Python backdoor that maintains control and enables data exfiltration.
Phase 3: Dual Exploitation
The same operatives simultaneously execute multiple threat vectors: deploying IT workers for legitimate-appearing employment to generate revenue, deploying malware through fake job interviews for espionage and cryptocurrency theft, and having employed IT workers introduce malware into company networks for additional exploitation.
INFRASTRUCTURE ANALYSIS & ATTRIBUTION
Bulletproof Hosting Providers
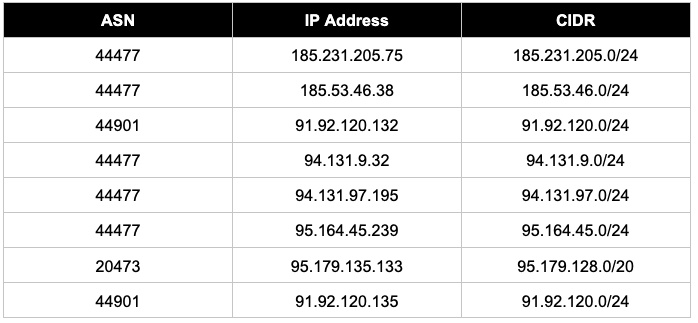
Analysis of BeaverTail/FerretRAT infrastructure reveals that Lazarus Group and associated DPRK threat actors favor specific bulletproof hosting providers. Evidence indicates extensive use of PQ Hosting Plus, formerly known as Stark Industries (AS 44477) and Belcloud (AS 44901), with multiple IP ranges exhibiting 100% infection rates, confirming their involvement in malicious operations.
PQ Hosting Plus (AS 44477)
PQ Hosting Plus, a well-known bulletproof hosting provider, was used at least 13 times in recent months for BeaverTail/FerretRAT campaigns. Infrastructure spans multiple countries, including Russia, Moldova, France, Gibraltar, and the Czech Republic. Multiple IP ranges demonstrate 100% infection rates, indicating exclusive use for malicious activity. Primary C2 Server: 95.164.17.24:1224 (linked to Contagious Interview campaign in October 2024, hosts Python downloader and InvisibleFerret backdoor).
Belcloud (AS 44901)
Belcloud, located in Bulgaria, is a smaller provider favored by multiple threat actors as a method to remain under the radar. The provider leases infrastructure to smaller entities, such as RedCluster (now operating as Vpsag in Cyprus). Analysis reveals that Belcloud's network is heavily utilized not only by Lazarus but also by APT42, APT34, APT35, Wizard Spider, Evil Corp, TeamSpy Crew, and Turla.
Infrastructure Indicators

RED FLAGS & WARNING INDICATORS
Application & Interview Stage
- Use of digital payment services linked to People's Republic of China
- Inconsistencies in personal information across profiles and platforms
- Requests for communication on separate platforms (Telegram, WhatsApp)
- Claims of attending only non-U.S. educational institutions
- Reused phone numbers (particularly VoIP) and email addresses across multiple applicants
Employment Stage
- Unusual payment requests or platform changes during onboarding
- Requests to change corporate device shipping address
- Failure to meet benchmarks or early placement on performance improvement plans
- Poor communication with managers despite technical competence
Technical Indicators
- Multiple people logged into accounts from same IP address simultaneously
- Accounts logged in continuously for one or more days
- Pattern of small unauthorized transactions over months
- Connections to Astrill VPN endpoints
RECOMMENDATIONS & MITIGATION
Identity Verification
- Implement enhanced background checks for remote workers
- Conduct video interviews requiring live interaction
- Verify educational credentials through official channels
Technical Controls
- Adopt preemptive cybersecurity tools such as Augur to bolster traditional Detection and Response ahead of first attacks and reduce alert noise in the SOC
- Block inbound/outbound traffic to identified malicious IPs and CIDRs
- Perform 60-day IOC retro hunt to identify historical activity
- Monitor connections to Astrill VPN endpoints
- Deploy EDR solutions with behavioral analytics
CONCLUSION
The DPRK IT Workers threat represents a critical convergence of traditional insider threat tactics and advanced persistent threat capabilities. Organizations face dual threats: direct financial loss through sanctions violations combined with risks of data theft, espionage, and extortion.
Infrastructure analysis reveals that Lazarus Group favors specific bulletproof hosting providers, particularly PQ Hosting Plus (AS 44477) and Belcloud (AS 44901), with multiple IP ranges demonstrating 100% infection rates. The infrastructure overlap across multiple threat actors indicates shared resources and predictable patterns.
The stakes are high: these operations directly fund North Korea's weapons programs while threatening intellectual property security worldwide. Vigilance, robust security practices, and information sharing remain essential to countering this evolving threat.
INDICATORS OF COMPROMISE
Network Indicators
Domain Indicators
- agencyhill99[.]com - Fake recruitment company
- mirotalk[.]net - Malicious video conferencing impersonation
C2 Infrastructure
Primary C2: 95.164.17.24:1224 (AS 44477)
Status: Active DPRK C2 linked to Contagious Interview
High-Risk Providers
- Stark Industries (AS 44477)
- Belcloud (AS 44901)
- Tier.Net
- Astrill VPN (favored by DPRK IT workers)




