AI agents are quickly becoming the new control plane for modern business, making them a high-value target. Combined with the urgency organizations and developers feel to operationalize these agents, AI is becoming a key attack surface and new vulnerabilities and attack strategies are being uncovered daily. Groups like NullBulge are actively probing agent connectors, API keys, and machine-to-machine trust paths to gain access, move laterally, and steal credentials for profit. Augur’s preemptive tracking identifies this threat infrastructure early so organizations can block it before it’s operationalized.
Who Is NullBulge?
NullBuge, which positions itself as a hacktivist group, is in fact a cybercriminal group operating primarily for financial gain, targeting enterprise AI pipelines and gaming companies. One of their key tactics is public repo poisoning, where they compromise publicly available code hosted on platforms like HuggingFace to reach downstream users and organizations. The group has also reportedly set its sights on Disney, in response to concerns about the company’s treatment of artists, actors, and graphic designers.
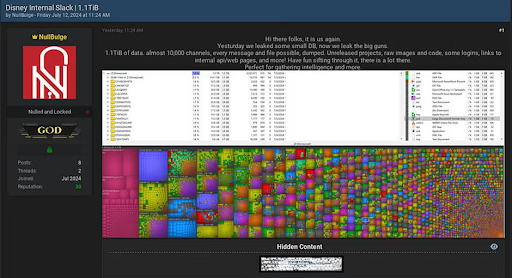
What Did Augur Know and When
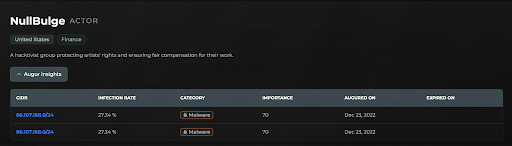

Augur identified IP 86.107.168.9, which is associated with NullBulge, as malicious nearly 2 years ago, providing some protection against NullBulge activities. We recommend blocking it and also blocking all IPs in its CIDR (86.107.168.0/24)
Why Should You Care?
On a more meta level, the NullBulge case is a clear warning that organizations deploying AI in production need to take a hard look at their exposure. The risk is rising fast due to high misuse potential, weak model and policy safeguards, and digital supply chain gaps across package registries, CI/CD plugins, and software update channels.
Between April and June 2024, SentinelOne confirmed multiple software supply chain attacks tied to NullBulge, where poisoned code was pushed into larger models and distributed through channels like GitHub, Discord, Reddit, and HuggingFace. NullBulge also downloaded trojanized versions of Anthropic and OpenAI-related libraries that quietly executed malicious code to steal Firefox and Chrome browser data via Network Security Services (NSS), and has continued spreading malicious scripts through Hugging Face updates.
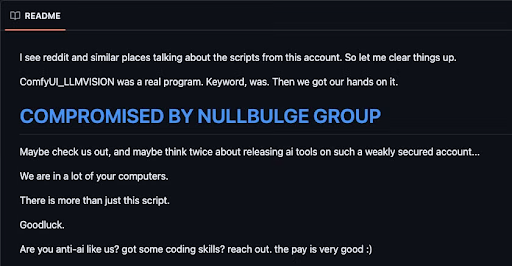
Disguised packages such as “SillyTavern Character Generator” and “Image Description with Claude Models and GPT-4 Vision” have also been used to slip harmful dependencies into the broader ML ecosystem, poisoning public projects and datasets at scale.
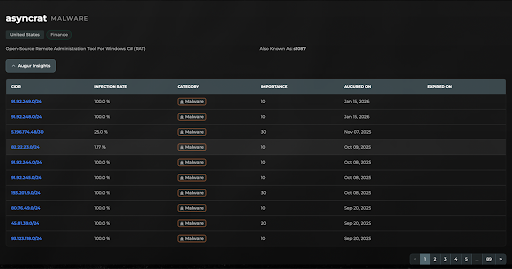
Tracking NullBulge and Associated Malware
In addition to tracking the NullBulge group, Augur also actively tracks the malware it commonly uses, including AsyncRAT and Xworm, to protect clients and support attribution. The group also sporadically deploys variants of the leaked LockBit 3.0 ransomware, although the alterations remain fairly simple. Despite this, Augur Security believes NullBulge to be a lower-skilled threat group that lacks any communication or direct links to the operators of LockBit ransomware.
NullBulge is the Warning Shot - Protect Your AI Workloads
NullBulge is a clear signal of where cyber risk is heading next: attackers aren’t just targeting endpoints, they’re targeting AI pipelines, trusted workflows, and the software supply chain that feeds them. If you’re deploying AI agents in production, the question isn’t if someone will probe your keys, repos, and update channels; it’s how quickly they’ll find a gap.
That’s why preemptive cybersecurity matters. Augur tracks threat infrastructure early, identifies malicious IPs and attacker-linked assets before they’re operationalized, and helps you block adversaries like NullBulge before the first credential is stolen or the first payload is delivered.
References
- NullBulge | Threat Actor Masquerades as Hacktivist Group Rebelling Against AI | SentinelOne
- AI Cyberattacks: How attackers target AI, and use AI against you | Wiz
- NullBulge Ransomware | WatchGuard Technologies
- Disney Slack Hack: Insider Threat Causes Massive Data Breach




